There was a time , where the number of computers on earth roughly exceeded 10, and the number of programmers was just around hundred or so. This wasn’t long ago , it has just been about 70 years , when ENIAC, the first computer was invented in 1946 [1] (early calculators and the abacus and early inventions that lead to the first computer are not accounted for, and big thanks to Alan Turing who is considered the father of programming) !
In these 70 years , we didn’t even have the Internet until just around the late 60’s , and the current internet infrastructure was never conceived with piracy and cyberattacks in mind [2].
The technology is so rapidly advancing and growing no doubt , and so is hardware and software : hundreds of programming languages , dozens of protocols , tens of operating systems , multi-core computers , CPUs , GPUs …
Through the ages, technology is constantly evolving, creating space for development, both good and bad..
Have you seen Mr. Robot? if it looks like dystopia or science-fiction, let me assure you friend, it is not.
White hat hackers around the globe are constantly fighting such attacks, from DDoS attacks that can make entire companies unable to perform services online, to crashing databases and stealing users passes and credits, to financial disruption, even to hacking airport systems, the consequences are deeply severe, so harmful, so destructive.
All of this is a bit terrifying for an experienced computer user, because we know how big is the amount of things we don’t know yet, but it is definitely more terrifying for any normal computer user, because you won’t even know what hit you ,and we have to stand up for a better secure world .
We should be all cheering for white-hat hackers, the “heroes” who save the day behind the scenes , but if we started talking about how vast the domain of IT is, and how rapidly it evolves , what does it really take to be a white-hat hacker?
what skills do I need to even the field and become on the same wave-length as black-hat hackers who seem to come up with new vulnerabilities every single day ?
White-Hat Hacker Skills
Do not panic, but a good efficient white-hat must have multiple skills in fields that are so different and so vast, from AI, to IoT, to Cloud Computing !
1. Artificial Intelligence
AI is no longer science-fiction, we are living in that future of self-driven cars, to fully automated inhuman factories[3], AI runs them all, it even runs our daily routine tasks such as parking cars, elevators and smart homes.
The domain is vast, and so are the vulnerabilities, imagine if a hacker can gain control over your car and crash it, or gain control over hotel systems or even your home !
But, as can black-hat hackers use AI and Machine Learning to exploit vulnerabilities, so can a white-hat !
Have you heard about Facebook who now monitors abusive posts and manages security threats through AI ?[4]
In the last F8 conference, Mark Zuckerberg announced that facebook is now using AI to fight back attacks [5] from spammers who just want money to fake accounts used to share fake information and shifting public opinion (the Us elections as an example).
So basically, the fastest solution to identify vulnerabilities and security flaws is to use AI and Machine learning.
2. Internet of Things
By 2020, the number of connected devices will exceed 31 billion devices worldwide [6].
From smart watches, to smart fridges, even to smart thermometers, every little gadget we have will be accessible online and connected to billions of others.
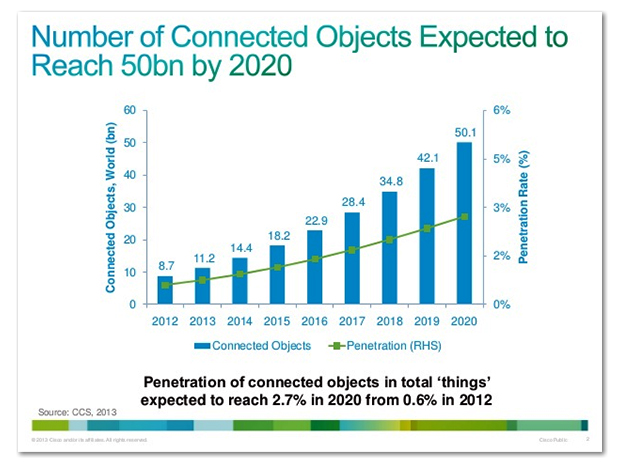
The threat is so big: what if a hacker can access not one or three of these, but millions ?
This can cause massive DDoS attacks, massive data collection, among dozens of threats.
Many cases can testify to this threat:
- In a North American casino, hackers managed to transfer data to a device in Finland, through an internet-connected thermometer from an aquarium in the lobby! [7]
- A team of researchers managed to hack and take control of a Jeep SUV using various entry points. The first infiltration was through the car’s Wi-Fi where they finally took control of the head unit’s system! [7]
Imagine the threat we are now facing, if a hacker manages to take control over airplanes and crush them into shopping centers and stadiums.. It is our job as white-hat hackers to stand up for this destructive behavior and insure a secure world where gadgets are used to make life easier and not to threaten it.
Every white-hat should have the right skills to fight IoT hackers, and fight them right from the beginning by making each newly developed system as secure as it can be through pentesting and Vulnerability Assessment to deal with flaws and risks.
3. Cloud Computing
The Cloud is the data mine of any hacker, keep this thought in mind, we will come back to it.
In 2006 , when large companies such as Google and Amazon began using “cloud computing” to describe the new paradigm in which people are increasingly accessing software, computer power, and files over the Web instead of on their desktops , cloud computing appeared [8] .
Since then, it has been the hottest buzzword in technology ever since, appearing on internet searches over 48 million times!
Who coined it? Who started it? When? you will get multiple answers , multiple dates , but what you have to know is the following : the implementation of cloud computing is bringing each organization closer to digital transformation , but it is a mine of passwords , emails , bank account details … if left unprotected , a hacker who gains access to such data , will cause great deal of threat !
In august 2013, yahoo had a data breach where 3 billion accounts – including email, Tumblr, Fantasy and Flickr – were hacked! [9]
Remember when we said that the cloud is the data mine of hackers? I guess now you get the picture
3 billion people were hacked in a single day that has to count for something, right?
The number of attacks on cloud-based accounts has increased by 300% as the security report published by windows shows [10].
If all this should count for something, it should be that white-hat hackers must have the right set of skills to fight this type of attacks and be able to secure the cloud services of a given company.
How can I become a white-hat hacker?
Being a security expert is definitely one of the best-paid jobs ever.
In 2018, the average payout to a Certified Ethical Hacker is $71,331 per annum, the salary ranges from $24,760 to $111,502, with a bonus payout that reaches $17,500 [11].
There is no doubt that security experts are the most wanted in the world , and with over 220 000 Certified Ethical Hacker in 145 countries [12] , The EC-Council is one of the best professional certification bodies in the world .
Its best-known certification is the Certified Ethical Hacker, which prepares you to penetrate networks and computer systems with the purpose of finding and fixing security vulnerabilities. [13]

Certification is achieved by taking the CEH examination after having attended training at an Accredited Training Center (ATC), and Tunisian Cloud is one of the top ATC in Tunisia and Africa.
Tens of candidates have chosen us as their ATC from all over Africa, with a success rate in the CEH examination of 100%.
With private access to the EC-Council platform for each candidate for 2 years, 5 days intensive training sessions (35 hours) and 1 month of online-coaching after the training session to prepare you for the examination, Tunisian Cloud is your ideal partner to go through CEH examination in Africa !

Check out our calendar , and don’t hesitate to contact us !
Sources :
- [1] https://www.computerhope.com/issues/ch000984.htm
- [2] https://en.wikipedia.org/wiki/Internet
- [3] https://www.businessinsider.com/tesla-completely-inhuman-automated-factory-2017-5
- [4] http://theconversation.com/can-facebook-use-ai-to-fight-online-abuse-95203
- [5] https://www.popsci.com/facebook-f8-developer-conference-2018
- [6] https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/
- [7] https://blog.eccouncil.org/ethical-hacking-like-never-before/
- [8] https://www.technologyreview.com/s/425970/who-coined-cloud-computing/
- [9] https://money.cnn.com/2017/10/03/technology/business/yahoo-breach-3-billion-accounts/index.html
- [10] https://www.microsoft.com/en-us/security/Intelligence-report
- [11] https://resources.infosecinstitute.com/certified-ethical-hacker-salary/
- [12] https://www.eccouncil.org/
- [13] https://en.wikipedia.org/wiki/Certified_Ethical_Hacker





